Reputable Managed IT Services Tampa for Your Business Demands
Reputable Managed IT Services Tampa for Your Business Demands
Blog Article
Boost Efficiency and SecurITy Through Managed IT Assistance Solutions
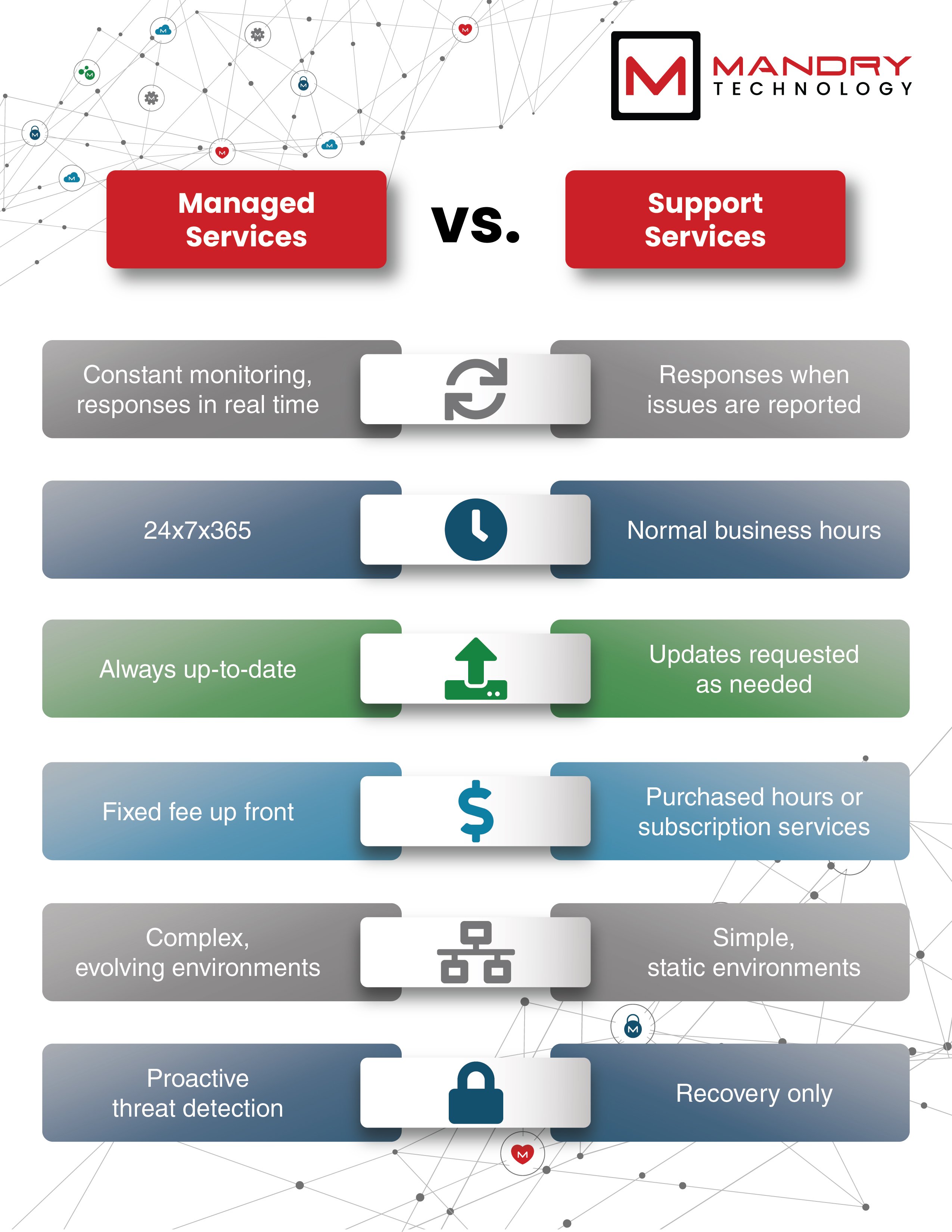
Handled IT sustain services have emerged as a crucial element in guaranteeing that companies can properly browse the intricacies of a digital environment. The synergy between boosting efficiency and enhancing safety and security through these solutions uses a strategic benefit that elevates functional performance and safeguards sensitive information.
Advantages of Managed IT Assistance
By supplying aggressive surveillance and upkeep, handled IT support solutions enhance functional performance and strengthen cybersecurity measures for businesses. These services aid in recognizing and resolving possible concerns prior to they rise, thereby lessening downtime and making sure seamless procedures. With regular tracking of networks, servers, and tools, managed IT support teams can discover anomalies immediately and take corrective activities swiftly. This aggressive technique not just protects against pricey disturbances however additionally improves general system efficiency.
Additionally, handled IT sustain services use services accessibility to a team of knowledgeable experts with varied knowledge - managed services Tampa. This implies that business can take advantage of specialized expertise and experience without the requirement for internal hiring and training. By outsourcing IT assistance, companies can focus on their core activities while leaving their technological facilities to qualified hands
In addition to functional effectiveness, managed IT sustain services play a crucial role in boosting cybersecurity defenses. In general, the positive surveillance and thorough assistance used by managed IT services are important for services looking to optimize efficiency and shield their electronic assets.
Boosted Performance Solutions
Carrying out innovative efficiency remedies can streamline workflows and optimize efficiency within an organization. Data analytics can aid identify fads, patterns, and locations for enhancement, making it possible for companies to make data-driven choices that drive productivity.
Enhanced productivity options additionally assist in much better cooperation amongst team participants. This promotes synergy, imagination, and innovation, eventually leading to enhanced efficiency end results.
Fortifying Information Security Actions
Just how can companies improve their data safety and security gauges to secure sensitive information and alleviate cybersecurity dangers successfully? By securing sensitive information, organizations can make certain that even if data is compromised, it continues to be indecipherable to unauthorized celebrations.
Moreover, carrying out multi-factor verification (MFA) includes an added layer of safety and security by requiring individuals to supply multiple types of verification before accessing delicate data. This substantially minimizes the danger of unauthorized accessibility, even if login credentials are endangered - managed services Tampa. Normal safety audits and susceptability assessments are additionally crucial to identify and resolve potential weak points in the organization's safety framework proactively
In addition, establishing stringent gain access to controls and individual authorizations helps limit the direct exposure of delicate data to just certified workers. By specifying that can access what details and applying a the very least privilege model, companies can lessen the danger of information breaches and expert threats. In general, a detailed method to data safety, consisting of security, MFA, normal audits, and gain access to controls, is vital in securing sensitive information and bolstering cybersecurity defenses.
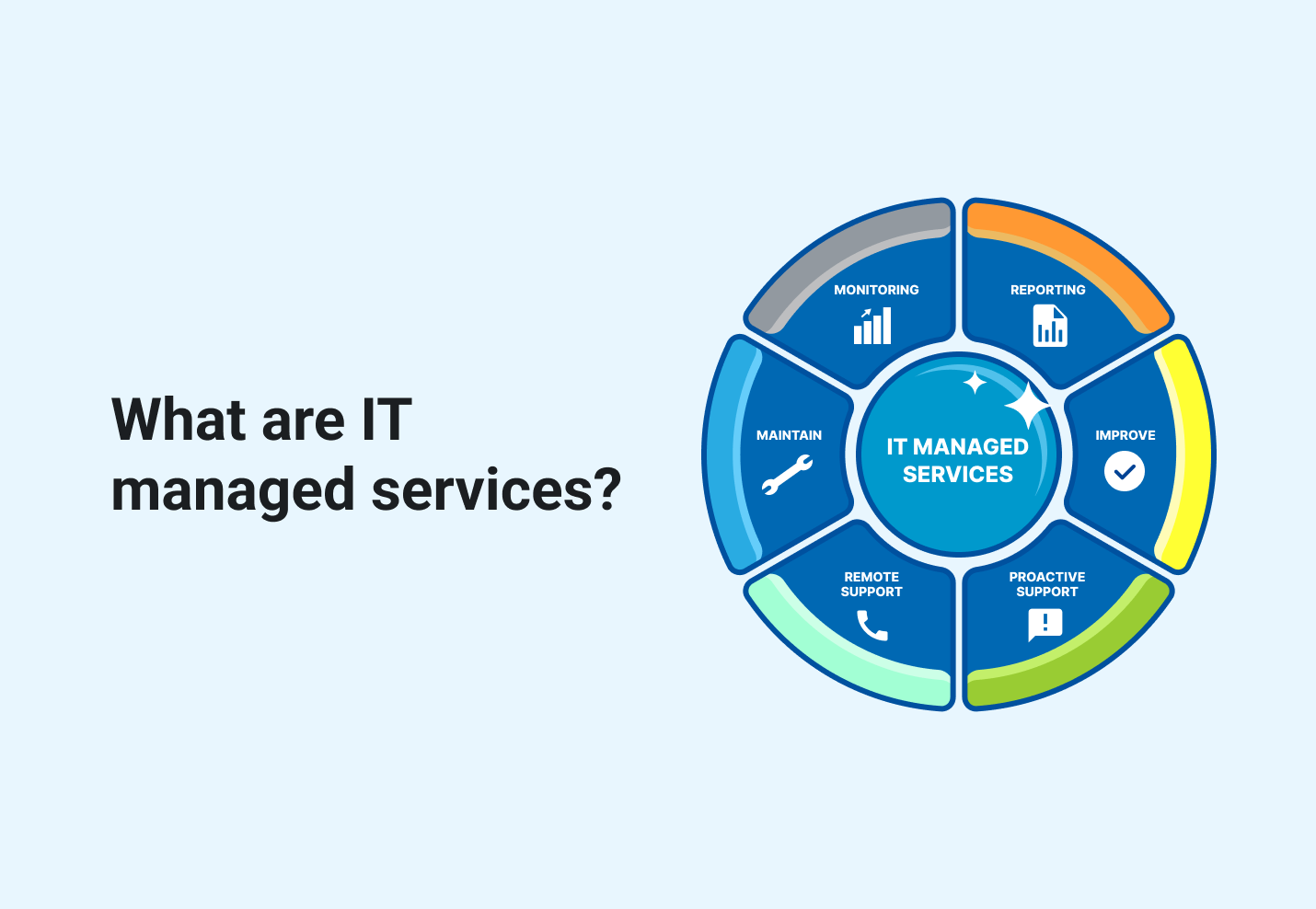
Proactive IT Monitoring and Upkeep
To fortify their general cybersecurity pose and guarantee continual operational performance, organizations must prioritize positive IT checking and upkeep as an important part of their managed IT sustain services. Positive IT keeping track of entails real-time tracking of systems, networks, and applications to identify and resolve possible concerns before they rise. By constantly monitoring IT facilities, companies can find abnormalities, vulnerabilities, or signs of putting at risk failings without delay, making it possible for speedy remediation activities to be taken. This aggressive method not just assists in protecting against costly downtime but additionally enhances safety by staying ahead of possible cyber dangers.
By proactively keeping IT systems, organizations can minimize the threat of vulnerabilities that might be exploited by cybercriminals. This preventative upkeep approach not just boosts total system efficiency however likewise makes sure that the organization's IT environment stays resistant against developing cyber dangers.
Cost-Effective IT Assistance Solutions
Efficient management of sources is vital for companies seeking to maintain a balance between high click this link quality IT support solutions and price performance. When taking into consideration cost-efficient IT support remedies, handled IT services stand out as a calculated option. These solutions provide a predictable prices model, enabling organizations to spending plan efficiently without unexpected expenses. Furthermore, by outsourcing IT sustain to a handled solution supplier, organizations can profit from the proficiency of a group of experts about his at a portion of the expense of hiring an internal IT department.
Managed IT services additionally assist in reducing downtime via aggressive monitoring and speedy issue resolution, inevitably saving services cash that would certainly have been shed during periods of lack of exercise. These solutions can scale up or down based on the organization's requirements, guaranteeing that businesses pay only for the services they need. By leveraging cost-efficient IT support remedies such as handled solutions, companies can optimize their IT procedures while keeping costs under control.
Conclusion
Report this page